A security vendor has discovered an attempt at using images posted to Twitter - memes - to allow criminals to remotely control malware on infected machines.
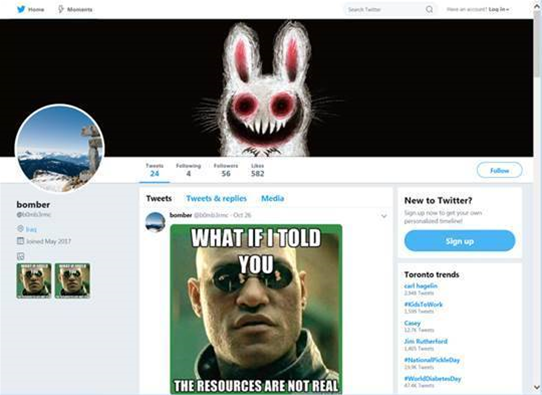
Trend Micro detailed the latest attempt at using steganography to hide malicious code within images to avoid detection, with the malware it has named TROJAN.MSIL.BERBOMTHUM.AA being coded to fetch JPG memes posted by specific Twitter accounts in October this year.
Two memes containing malicious code were posted to the @b0mb3rnc Twitter account, which was closed by the social media company on December 14 Australian time.
The malware appears to be a half-baked as it stands currently: the memes only contained a "/print" command that directed the malware to take screenshots; an hyper text transfer protocol link would then be retrieved from the Pastebin copy and paste site, which pointed to a server address.
However, the Pastebin link pointed to an RFC 1918 private internet protocol address, that can't be reached outside internal networks so the screenshot transfers would not work.
Trend Micro's analysis of the malware showed that apart from taking screenshots, it can retrieve a list of running processes, account name of the logged in user, and filenames in specific directories on an infected machine.
The malware can be instructed to capture clipboard content as well.
At this stage, it is not clear how the malware is spread beyond it not being distributed via Twitter, Trend Micro said.
"Stegomalware" that weaponises seemingly innocuous images, videos, text files and other digital content is a growing threat vector that emerged some years ago.

.jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)

_page-0001_(1).jpg&w=100&c=1&s=0)
 Integrate
Integrate
















